Longer LDAPS Certificates
Create a New Kerberos Authentication Certificate with Extended Validation Period¶
Follow these steps to create a Kerberos authentication certificate with a longer validation period:
Configure Certificate Authority for Extended Validity¶
- Open Command Prompt as Administrator:
-
On the Certificate Authority (CA) server, open CMD.exe with administrative privileges.
-
Set Validity Period Units:
- Replace X with the desired number of units (e.g., Years, Months) for certificate validity.
- Note: The validity period cannot exceed the CA certificate’s validity.
Restart the Certificate Authority with the commands:
From the Certificate Authority console, right-click “Certificate Template” and click “Manage. Right-click the Kerberos Authentication template and select “Duplicate Template”. Click the “General” tab and give the template a friendly name and change the Validity period to the desired length. Be advised that the certificate can not have a validity period longer than the CA-certificate.
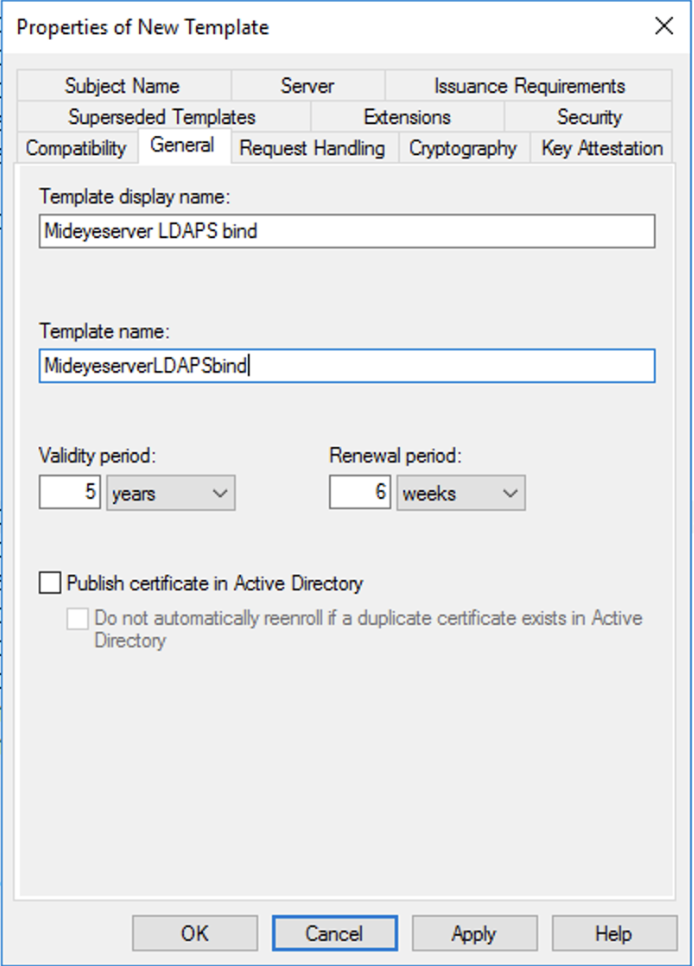 Change the validity time of the new template
Change the validity time of the new template
Select the “Security” tab and add the computer account of the Domain Controller. Click “OK” and close the “Certificate Templates Console”.
Again, from the “Certificate Authority” console right-click “Certificate Template” and select “New” followed by “Certificate Template to Issue”
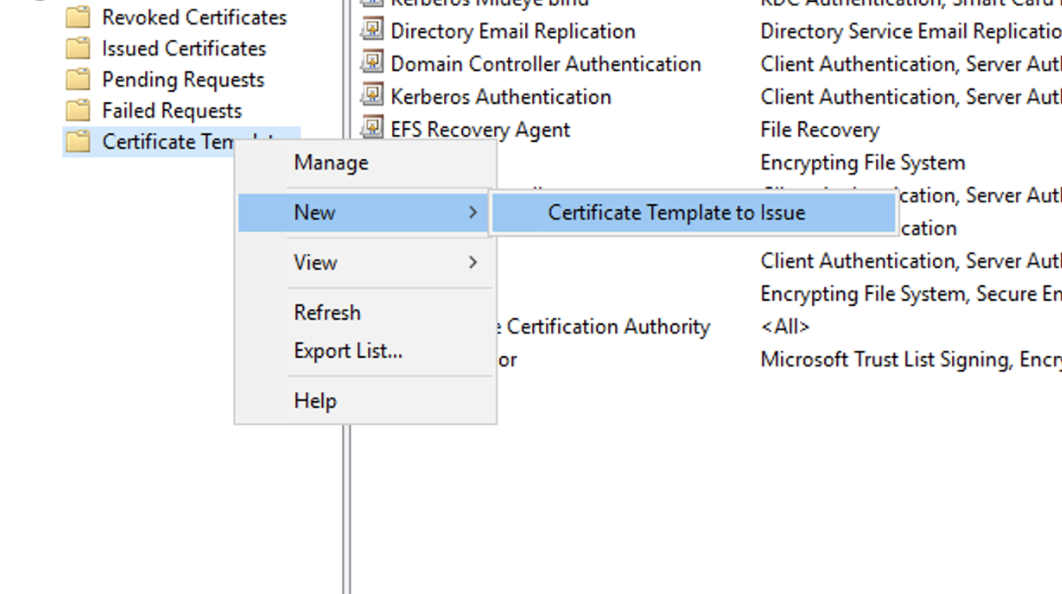
Issue a new template
Select the created template and click “OK”. Restart the Certificate Authority service.
From the Domain Controller, execute mmc.exe from the start menu. Click “Add/Remove snap-in” from the File menu and select Certificate followed by “Computer Account”. Select “Local Computer” and click “OK”. Expand Certificate –> Personal and right-click “Certificates” –> “All tasks” –> “Request New Certificate”. Select the certificate template created above and click “Enroll”.
The last step is to update the certificate in the Mideye Server. Navigate to Configuration followed by LDAP-profiles. Click modify on the LDAP server. Click “Fetch Certificate” and import the new certificate with a longer validity time.
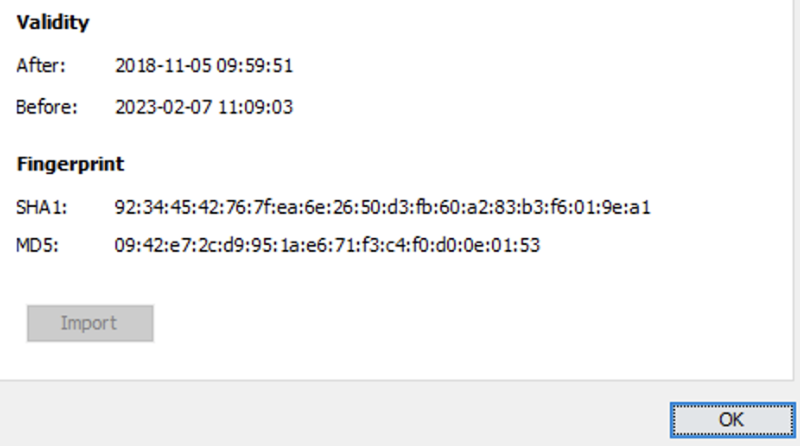 Import the new Kerberos authentication certificate Save the configuration.
Import the new Kerberos authentication certificate Save the configuration.